这是一个创建于 1149 天前的主题,其中的信息可能已经有所发展或是发生改变。
我有两个局域网,分别是 192.168.203.0/24 192.168.211.0/24 ,两个局域网网内分别有一台设备接入 WireGuard, 通过 WireGuard 打通,WireGuard 节点网段为 10.0.110.0/24 ,一切 OK 。
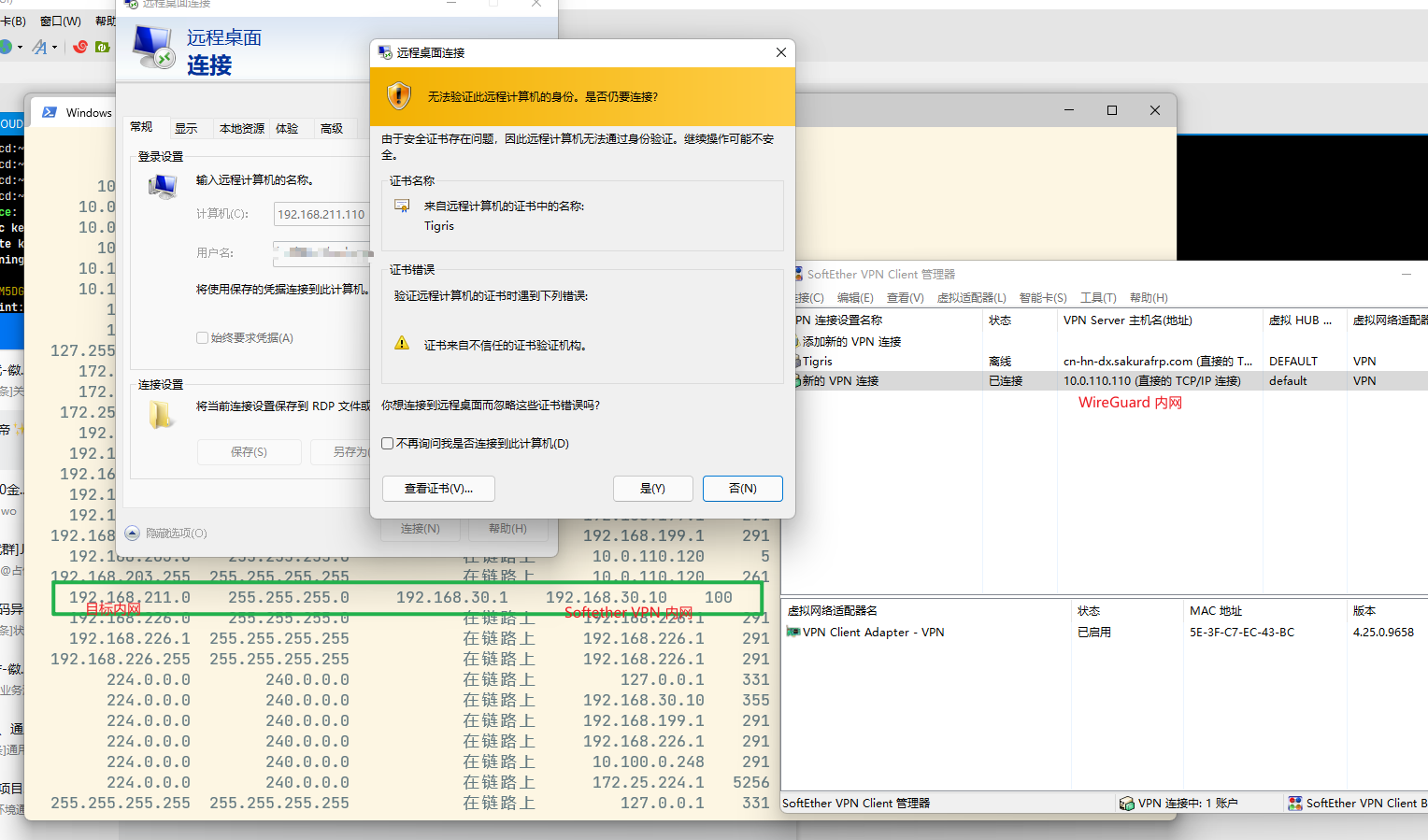
但是最近,10.0.110.110 ( Win10 设备)无法通过远程桌面连接了,ping 以及 http 都是能正常的:
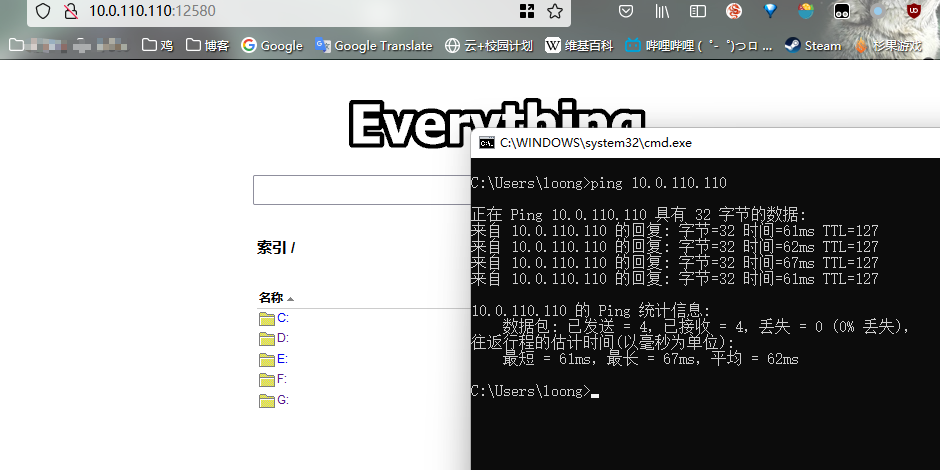 tcp ping 试了,就 3389 不通:
tcp ping 试了,就 3389 不通:
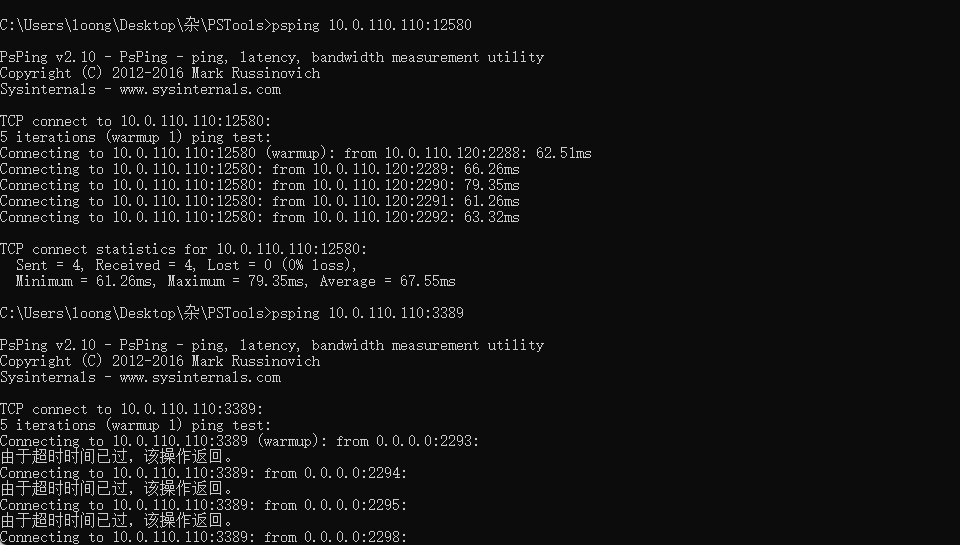 于此同时,我通过 10.0.110.110:5555 连上 softether vpn ,在 softether vpn 内是可以访问的:
于此同时,我通过 10.0.110.110:5555 连上 softether vpn ,在 softether vpn 内是可以访问的:
一开始以为是 Windows 防火墙问题,但是关闭防火墙后问题依旧。换个思路让 10.0.110.100 ( Ubuntu )用 ssh 监听 3389 端口,果然又不通了:
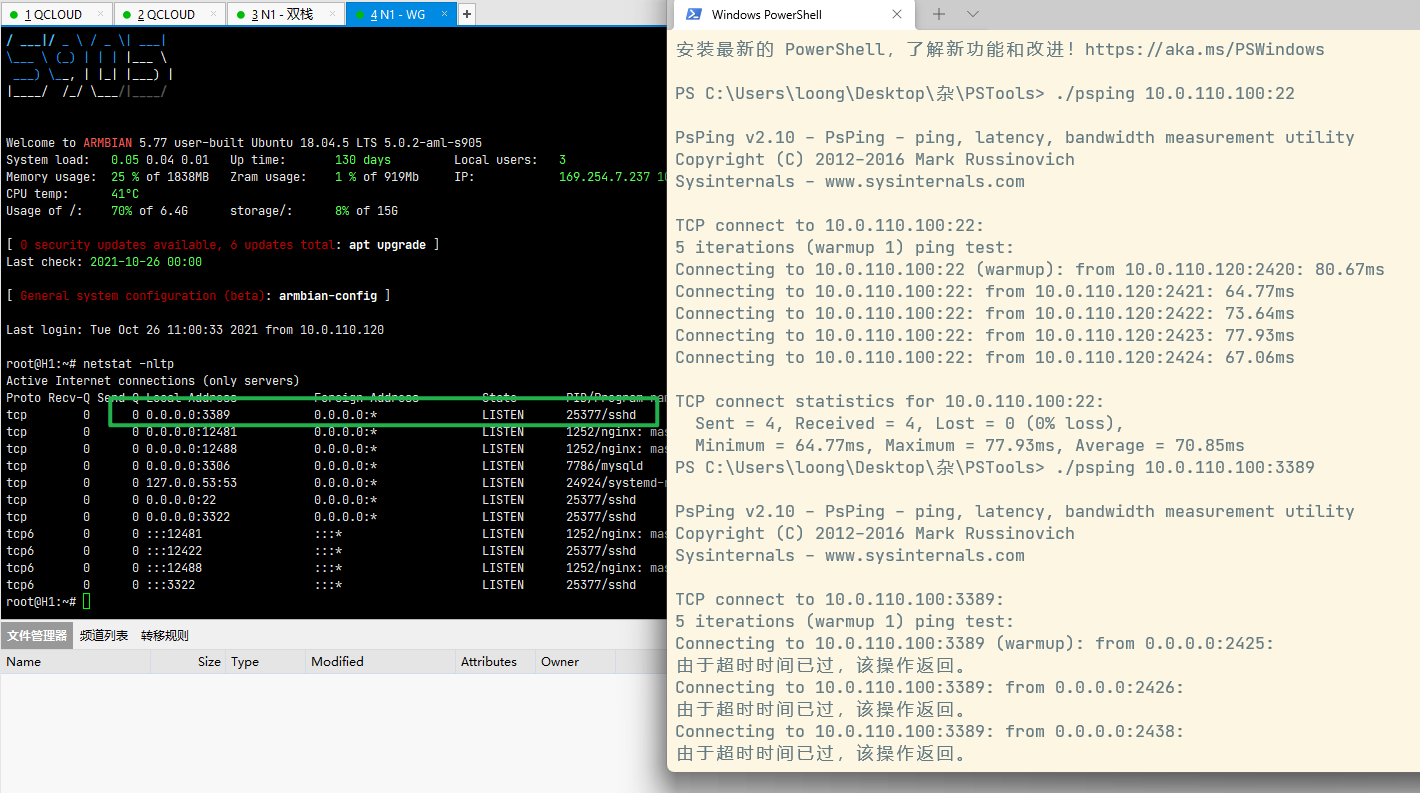
基本判断问题在中转节点,但是检查了各处配置,没看出问题:
- route
ubuntu@cd:~$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default _gateway 0.0.0.0 UG 100 0 0 eth0
10.0.12.0 0.0.0.0 255.255.252.0 U 0 0 0 eth0
10.0.110.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
192.168.203.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.211.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
- ifconfig
wg0: flags=209<UP,POINTOPOINT,RUNNING,NOARP> mtu 1200
inet 10.0.110.10 netmask 255.255.255.255 destination 10.0.110.10
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 1000 (UNSPEC)
RX packets 16195152 bytes 5253025408 (5.2 GB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 15604436 bytes 5264336568 (5.2 GB)
TX errors 165 dropped 2097 overruns 0 carrier 0 collisions 0
- iptables
ubuntu@cd:~$ sudo iptables -nvL
Chain INPUT (policy ACCEPT 64105 packets, 17M bytes)
pkts bytes target prot opt in out source destination
3080 3782K udp2rawDwrW_ae1afd8c_C0 tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:12581
66M 12G ufw-before-logging-input all -- * * 0.0.0.0/0 0.0.0.0/0
66M 12G ufw-before-input all -- * * 0.0.0.0/0 0.0.0.0/0
63M 12G ufw-after-input all -- * * 0.0.0.0/0 0.0.0.0/0
63M 12G ufw-after-logging-input all -- * * 0.0.0.0/0 0.0.0.0/0
63M 12G ufw-reject-input all -- * * 0.0.0.0/0 0.0.0.0/0
63M 12G ufw-track-input all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 30583 packets, 12M bytes)
pkts bytes target prot opt in out source destination
213M 73G DOCKER-USER all -- * * 0.0.0.0/0 0.0.0.0/0
213M 73G DOCKER-ISOLATION-STAGE-1 all -- * * 0.0.0.0/0 0.0.0.0/0
94M 57G ACCEPT all -- * docker0 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
13852 817K DOCKER all -- * docker0 0.0.0.0/0 0.0.0.0/0
105M 11G ACCEPT all -- docker0 !docker0 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- docker0 docker0 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-before-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-before-forward all -- * * 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-after-forward all -- * * 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-after-logging-forward all -- * * 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-reject-forward all -- * * 0.0.0.0/0 0.0.0.0/0
14M 4567M ufw-track-forward all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 69257 packets, 23M bytes)
pkts bytes target prot opt in out source destination
72M 23G ufw-before-logging-output all -- * * 0.0.0.0/0 0.0.0.0/0
72M 23G ufw-before-output all -- * * 0.0.0.0/0 0.0.0.0/0
69M 22G ufw-after-output all -- * * 0.0.0.0/0 0.0.0.0/0
69M 22G ufw-after-logging-output all -- * * 0.0.0.0/0 0.0.0.0/0
69M 22G ufw-reject-output all -- * * 0.0.0.0/0 0.0.0.0/0
69M 22G ufw-track-output all -- * * 0.0.0.0/0 0.0.0.0/0
Chain DOCKER (1 references)
pkts bytes target prot opt in out source destination
138 6976 ACCEPT tcp -- !docker0 docker0 0.0.0.0/0 172.17.0.3 tcp dpt:8080
154 8272 ACCEPT tcp -- !docker0 docker0 0.0.0.0/0 172.17.0.2 tcp dpt:1358
10841 643K ACCEPT tcp -- !docker0 docker0 0.0.0.0/0 172.17.0.4 tcp dpt:3306
157 8407 ACCEPT tcp -- !docker0 docker0 0.0.0.0/0 172.17.0.5 tcp dpt:27017
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
pkts bytes target prot opt in out source destination
105M 11G DOCKER-ISOLATION-STAGE-2 all -- docker0 !docker0 0.0.0.0/0 0.0.0.0/0
213M 73G RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain DOCKER-ISOLATION-STAGE-2 (1 references)
pkts bytes target prot opt in out source destination
0 0 DROP all -- * docker0 0.0.0.0/0 0.0.0.0/0
105M 11G RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain DOCKER-USER (1 references)
pkts bytes target prot opt in out source destination
213M 73G RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain udp2rawDwrW_ae1afd8c_C0 (1 references)
pkts bytes target prot opt in out source destination
3080 3782K DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ufw-after-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-logging-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-logging-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-logging-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-after-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-logging-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-logging-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-logging-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-before-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-reject-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-reject-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-reject-output (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-track-forward (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-track-input (1 references)
pkts bytes target prot opt in out source destination
Chain ufw-track-output (1 references)
pkts bytes target prot opt in out source destination
- ufw
ubuntu@cd:~$ sudo ufw status
Status: inactive
在服务端用 tcpdump 进行抓包,是这么个结果:
实在没辙了,各位大佬有别的排查思路么?不然就只能给 RDP 换端口,或者套一层 softether vpn 用了,难顶
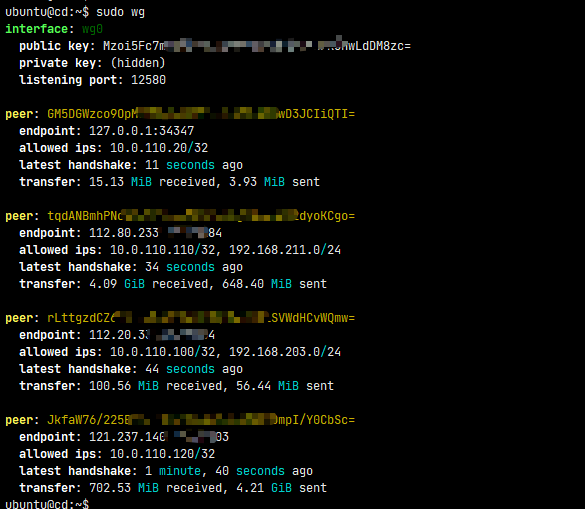
附上中转节点 wg 配置:
第 1 条附言 · 2021-10-26 13:53:22 +08:00
破案了,nat prerouting 有条针对 3389 的规则,果然还是 iptables 的问题😭
iptables -nvl 得记得加 -t 把各个表都看看,或者用 iptables-save 看
iptables -nvl 得记得加 -t 把各个表都看看,或者用 iptables-save 看
1
zhangsanfeng2012 2021-10-26 11:39:25 +08:00
在中转节点和 10.0.110.110 上同时抓包看看
|
2
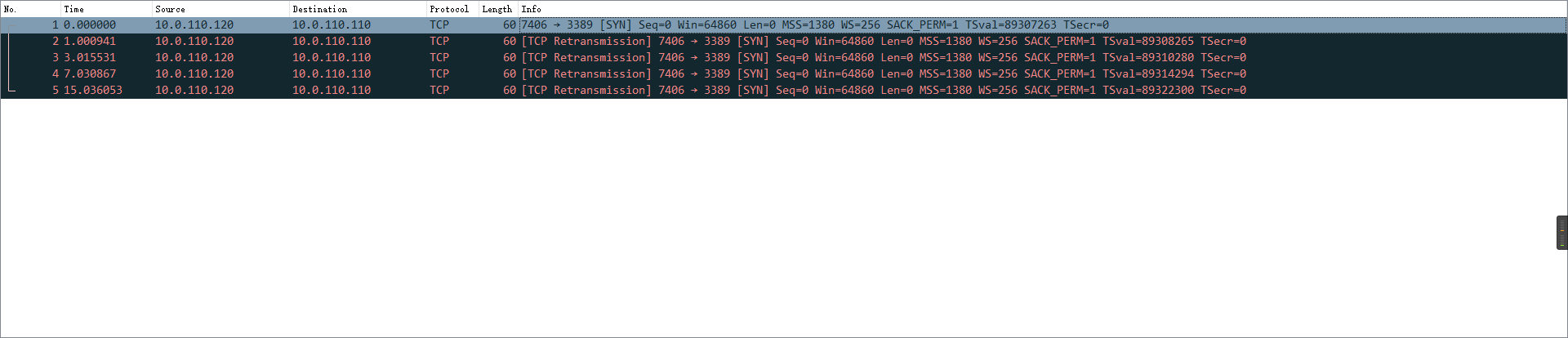
olaloong OP @zhangsanfeng2012 有试的,比如从 10.0.110.120 访问 10.0.110.110:3389 ,10.0.110.120 和 中转节点都是一次 SYN 四次重传,10.0.110.110 没收到包
* 10.0.110.120 [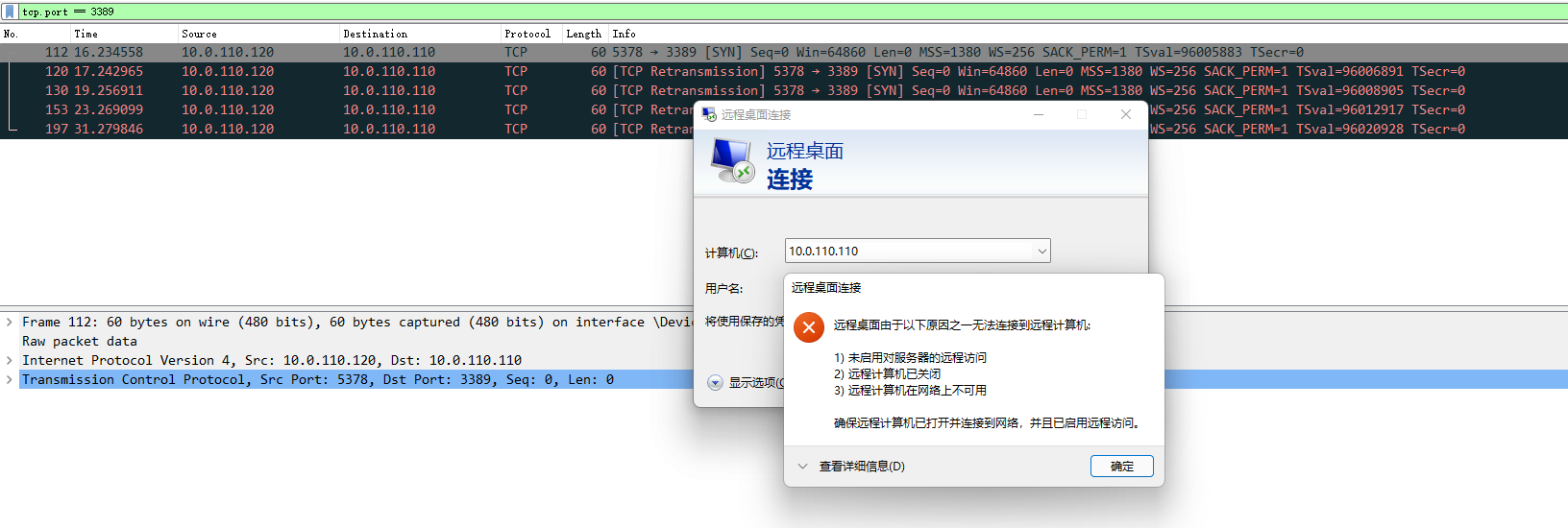]( https://imgtu.com/i/5ICknA) * 10.0.110.10 中转节点 []( https://imgtu.com/i/5ICU9U) * 10.0.110.110 空白 |
3
1423 2021-10-26 12:09:05 +08:00
不走隧道,10.0.110.110 机器上的 3389 可以通么
|
5
zhangsanfeng2012 2021-10-26 12:52:54 +08:00 via Android @olaloong 中转节点 wg0.conf 和 iptables-save 贴出来看看
|
6
zhangsanfeng2012 2021-10-26 12:54:42 +08:00 via Android
@zhangsanfeng2012 还有 ip rule
|
7
olaloong OP |
8
dylanninin 2021-10-26 14:18:42 +08:00
@olaloong 中转节点里抓包后,wireshark 过滤器改一改,用 `ip.dst == 10.0.110.110` ,看看完整的信息是怎样的
|
9
U8Gu9Hs3H3jD 2021-11-10 14:16:48 +08:00
zan
|